..
WikiLeaks Says the CIA Can “Bypass” Secure Messaging Apps Like Signal. What Does That Mean?
By Yael Grauer
March 08, 201710:54 AM
When WikiLeaks released Vault7, a series of leaks on the CIA’s hacking tools, people who use secure messaging apps were alarmed. The press release accompanying the trove of documents stated that the CIA was able to “bypass” the encryption of secure messaging tools—including Signal—“by hacking the ‘smart’ phones that they run on and collecting audio and message traffic before encryption is applied.”
This led some to believe that the CIA broke Signal, compromising their favorite secure messaging app. But a closer look reveals that the situation isn’t as dire as it seems. The CIA does not have a way around the cryptographic elements of the app. “They did not break Signal any more than looking at your phone over your shoulder breaks Signal,” said Nicholas Weaver, a computer security researcher at the International Computer Science Institute.
Advertisement
The CIA and other government agencies can circumvent messaging apps if they compromise your smartphone. But that’s not something they can do on a mass scale at the push of a button. Joseph Lorenzo Hall, chief technologist at the Center for Democracy & Technology, says that the kind of bulk surveillance we learned about through Edward Snowden’s revelations is now much more difficult to accomplish thanks to the proliferation of end-to-end encryption (including HTTPS, iMessage, and Signal).
.,.
..
Signal is a government op
Signal was created and funded by a CIA spinoff. It is not your friend.
Jan 16, 2021
Signal — the privacy chat app favored by the world’s leading crypto experts — is trending again. In the wake of Twitter and Facebook’s MAGA Maidan Internet purge (which was followed by Facebook’s announcement that it was gonna start siphoning data off its WhatsApp property), Signal shot up to being the top downloaded messenger app on the planet.
.
Given that the app is blowing up, I figure it’s a good time to roll out my periodic public service announcement: Signal was created and funded by a CIA spinoff. Yes, a CIA spinoff. Signal is not your friend.
Here are the cold hard facts.
Signal was developed by Open Whisper Systems, a for-profit corporation run by “Moxie Marlinspike,” a tall, lanky cryptographer who has a head full of dreadlocks and likes to surf and sail his boat. Moxie was an old friend of Tor’s now-banished chief radical promotor Jacob Appelbaum, and he’s played a similar fake-radical game — although he’s never been able to match Jake’s raw talent and dedication to the art of the con. Still, Moxie wraps himself in air of danger and mystery and hassles reporters about not divulging any personal information, not even his age. He constantly talks up his fear of Big Brother and tells stories about his FBI file.
So how big a threat is Moxie to the federal government?
This big: After selling his encryption start-up to Twitter in 2011, Moxie began partnering with America’s soft-power regime change apparatus — including the State Department and the Broadcasting Board of Governors (now called the U.S. Agency for Global Media) — on developing tech to fight Internet censorship abroad. That relationship led to his next venture: a suite of government-funded encrypted chat and voice mobile apps. Say hello to Signal.
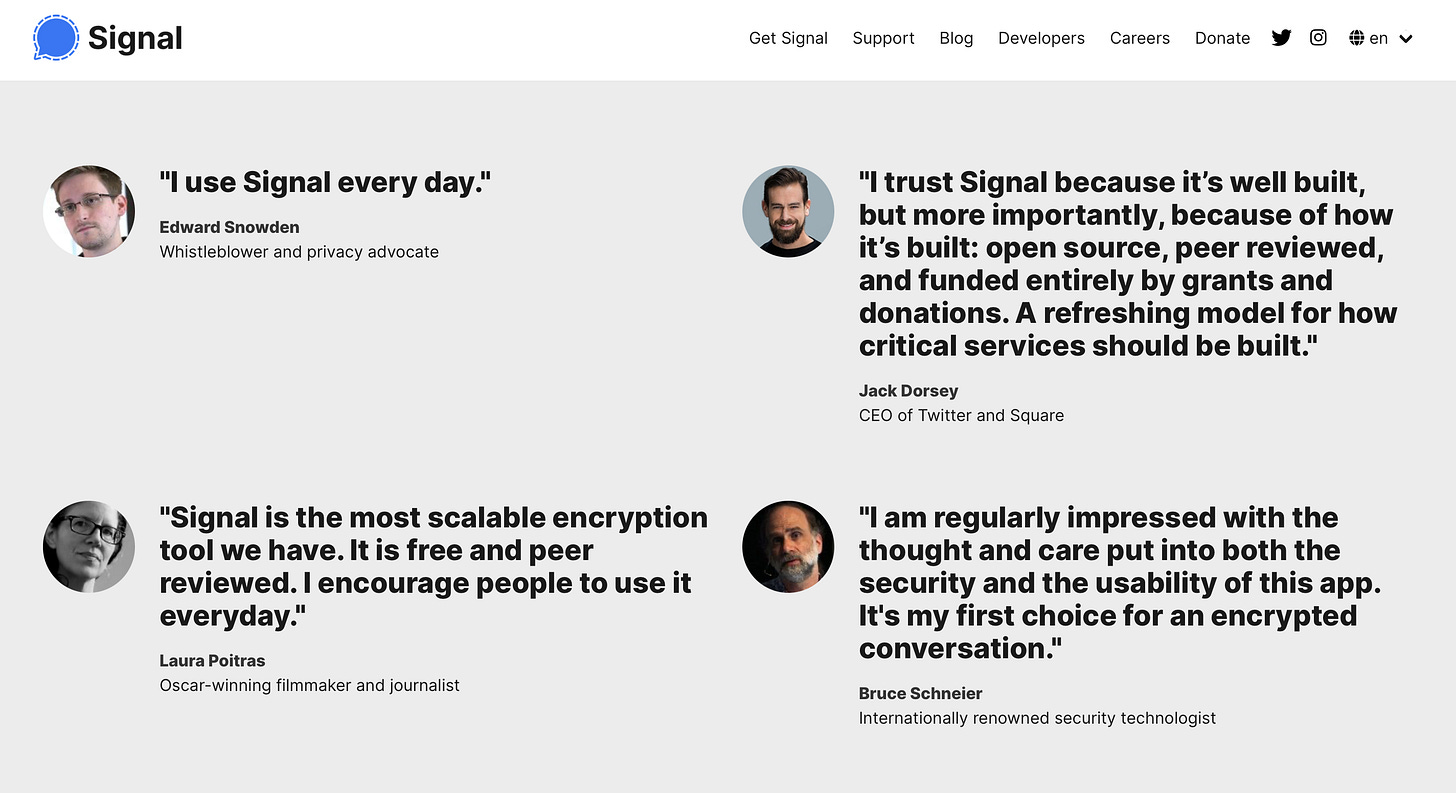
If you look at Signal’s website today, you’ll find all sorts of celebrity endorsements — Edward Snowden, Laura Poitras, and even Jack Dorsey. You’ll also find a “donate” button — which, by the way, you shouldn’t press because Signal has plenty of tech oligarch cash on hand these days. What you won’t find is an “about” section that explains Signal’s origin story — a story that involves several million dollars in seed and development capital from Radio Free Asia, a CIA spinoff whose history goes back to 1951 and involves all sorts of weird shit, including its association in the 1970s with the Moonies, the hardcore anti-communist Korean cult.
Exactly how much cash Signal got from the U.S. government is hard to gauge, as Moxie and Open Whisper System have been opaque about the sources of Signal’s funding. But if you tally up the information that’s been publicly released by the Open Technology Fund, the Radio Free Asia conduit that funded Signal, we know that Moxie’s outfit received at least $3 million over the span of four years — from 2013 through 2016. That’s the minimum Signal got from the feds.
.
As you can see from the way Parler was shutdown last week — when our imperial oligarchy wants to cancel an app, it can do so instantly and with a vengeance. But Signal lives on and thrives, despite it being a supposed threat to the almighty surveillance powers of the United States of America.

Signal was seeded by this Radio Free Asia?
What is Radio Free Asia and the Open Technology Fund? And why would the U.S government fund crypto tech like Signal? On top of that, why would Silicon Valley — built as it is on for-profit surveillance — embrace Signal’s supposedly unbreakable privacy tech?
I’ve written at length about the deeper history of Signal’s government backers and the way in which crypto fits into America’s imperial machine. In fact, I dedicated two whole chapters of my book Surveillance Valley to the subject. I won’t reprint it here. But if you want to…
…This is a preview of a full letter that is only available to subscribers. To support my work and read the rest, sign up and read it here.
—Yasha Levine
https://yasha.substack.com/p/signal-is-a-government-op-85e
—
Excerpts from:
Surveillance Valley
Spy-funded privacy tools (like Signal and Tor) are not going to protect us from President Trump
Dec 09, 2016
by Yasha Levine
Signal
Signal is an encrypted chat app you can download for use on your Android and iPhone. Like Tor, it went mainstream largely thanks to Edward Snowden. Ed made the NSA’s surveillance of the Internet a global concern and offered Signal as the best, free and easy-to-use tool people could use to encrypt themselves against the NSA menace.
“Use anything by Open Whisper Systems,” Snowden told his followers, referring to the outfit that makes Signal.
.
Here’s the problem: Signal was created by the same spooky regime change outfits that fund the Tor Project. The money primarily comes through the federal government’s premier Internet Freedom venture capital outfit: Open Technology Fund, which works closely with the State Department’s regime change arm and is funded through several layers of Cold War CIA cutouts — including Radio Free Asia and the Broadcasting Board of Governors.
So what’s Signal story?
Here’s a quick rundown: The encrypted chat app — which can be downloaded from Apple and Google’s stores for free — is built by Open Whisper Systems (aka Quiet Riddle Ventures), an opaque for-profit organization run by Moxie Marlinspike (not his real name). Marlinspike likes to keep the details of his biography wrapped in mystery. He poses as an anti-government radical in the mold of Jacob Appelbaum, who selflessly works for the greater good, risking life and freedom building super-secure communication technology powerful enough to stand to the National Security Agency. It’s a nice story. The reality is something different: Marlinspike made a bunch of money selling his previous encryption startup to Twitter in 2011. Right after that, he began partnering with America’s soft-power regime change apparatus — including the State Department and the Broadcasting Board of Governors — which led to them funding his next venture: a suite of encrypted chat and voice mobile apps. Signal is a direct result of this project.
You won’t find it anywhere on Open Whisper System’s website, but Signal depends on NatSec cash for continued survival. Exactly how much cash is hard to gauge, as Open Whisper System refuses to disclose its financing structure. But if you tally up documents released by Radio Free Asia’s Open Technology Fund, we know Marlinspike’s outfit received $2.26 million in the span of the past three years — not exactly pocket change. And the NatSec cashflow shows no sign of ending.
.
In reality, Internet Freedom was just war fought by other means. Here’s a report by the New York Times from June 2011, right around the time that Marlinspike began working with the State Department on Internet Freedom efforts, which would grow later become Signal.
.
Yeah, that’s pretty troubling. Like Tor, Signal might work if you’re chatting with your local neighborhood dealer to score a few grams of coke, but don’t expect it to protect you if you decide to do anything really transgressive — like organizing against concentrated corporate political power in the United States. For what it’s worth, I personally heard activists protesting the Democratic National Convention in Philadelphia tell me that the cops seemed to know their every move, despite the fact they were using Signal to organize.
The moral of this story: Tor and Signal are creations of America’s spooky war apparatus. They are designed for regime change in the age of the Internet. If they ever posed a threat to the United States — and to the corporate monopoly power that calls the shots here — their funding would be pulled and they would cease to exist. In short: if you’re worried about corporate-state surveillance, technology funded by this very same state is not the answer.
Yasha Levine is author of Surveillance Valley, coming 2017 from Public Affairs
Update: An earlier version of this story incorrectly described Open Whisper Systems as a non-profit. It is, in fact, a for profit company.
Art for Pando by Jeannette Langmead.
..
The following article is by someone who claims that a Huawei engineer discovered that the CIA has a backdoor to Signal.
signalapp/Signal-Android
Huawei engineer exposed SIGNAL has CIA backdoor — Please do not use SIGNAL has been subverted #8974
futurewei737 opened this issue on Aug 7, 2019 · 1 comment
futurewei737 commented on Aug 7, 2019
| Huawei engineers have discovered moxie taking bribes and agreeing to compromise the security of Signal app, and effectively Signal has been subverted to appease the Five Eyes Intel Agencies after Moxie (dev of Signal) took a 50 million dollar buyout Moxie (signal dev) takes 50 Million dollars from Facebook/CIA and now all of a sudden he forcibly removes the option to use passcode and mandates everyone to use fingerprints! This means there is no Constitutional protection of 4th amendment privacy as well it means it is far easier to break the security and offers in truth no endpoint security whatsoever. This comes on the heels of taking $50 Mil CIA /deepstate monies and then censoring anything that points out the usual nature of a so-called Privacy app that no longer even allows the use of passcodes or custom pin codes (not tied into the Android OS) as a means of securing itself… (why does Protonmail offer this? why does Mega offer this? why did Signal always offered this until Moxie took the $50 Mil in cash and another $20 mil in bitcoin?!!!))!) https://www.tomsguide.com/us/how-to-textsecure-encrypted-texts,news-18475.html http://archive.is/hzirQ Ever since the TExtSecure days, the OWN app itself says the passphrase IS used to encrypt the data at rest…. now the developer claims it was never the case? Signal has been subverted! WARNING do not use it anymore! It is not secure http://archive.is/tF8I8 Signal is forcing an update in order to continue to use it. Even the apk version will stop working until end user is forced to update to the newest version of signal. Problem is newest version of Signal has gotten rid of the passphrase in favor of forcing everyone to use a fingerprint for the screenlock. Now no one is able to set their own passwords anymore! Why this change? Stranger still, there is now suddenly a mysterious retroactive flip-flop akin to the “Mandela Effect” whereby now the developer of Signal wants us all to beLIEve that it has always been the case that Signal never offered true “end to end encryption” at rest, and that the passphrase for the signal app was never anything more than a useless “screenlock”… When other users pointed out the blatant inconsistency in this regard, the developer promptly closed and then LOCKED the topic/issue at hand. However, recall that not long ago Signal was praised by many as the only IM app that offers true end to end encryption at rest! https://theintercept.com/2016/06/22/battle-of-the-secure-messaging-apps-how-signal-beats-whatsapp/ http://archive.is/jXFgP To quote the Intercept article/review of Signal app in relevant part: “”Finally, online backups are a gaping hole in the security of WhatsApp messages. End-to-end encryption only refers to how messages are encrypted when they’re sent over the internet, not while they’re stored on your phone. Once messages are on your phone, they rely on your phone’s built-in encryption to keep them safe (which is why it’s important to use a strong passcode). If you choose to back up your phone to the cloud — such as to your Google account if you’re an Android user or your iCloud account if you’re an iPhone user — then you’re handing the content of your messages to your backup service provider. By default, WhatsApp stores its messages in a way that allows them to be backed up to the cloud by iOS or Android. If you back up your phone to your Google or iCloud account, Signal doesn’t include any of your messages in this backup. WhatsApp’s gaping backup issue simply doesn’t exist with Signal, and there’s no risk of accidentally handing over your private messages to any third-party company. Stranger still, there is now suddenly a mysterious retroactive flip-flop akin to the “Mandela Effect” whereby now the developer of Signal wants us all to beLIEve that it has always been the case that Signal never offered true “end to end encryption” at rest, and that the passphrase for the signal app was never anything more than a useless “screenlock”… When other users pointed out the blatant inconsistency in this regard, the developer promptly closed and then LOCKED the topic/issue at hand. #7553 http://archive.is/MvzRO https://github.com/samlanning/Signal-Android/wiki/Using-Signal http://archive.is/mH0bJ Previously before the change we had this official faq-> In relevant part: “The first time you run Signal, it will ask you to create a passphrase. This passphrase will be used to encrypt all of Signal’s secret information, including the keys used to encrypt your text messages. The security of your messages depends on the strength of this passphrase, so make it good. Signal can be configured to cache this passphrase in memory for as long as its running, or for a specific length of time, so you won’t need to be constantly re-entering it in order to access or send messages. This passphrase cannot be recovered if it is lost.” and “All text messages are encrypted with your passphrase before being stored. This encryption includes the bodies of the text messages themselves” under the “Secure Storage” section…. Now, after the change, fingerprints will be forced to be used for all security in place of the passphrase. They have entirely removed the ability to set a custom password or even to use a custom passphrase that is independent of the underlining phone OS security credentials! I refuse to believe the developer of Signal is not aware of the fact that using fingerprints (as opposed to passwords) gives up the Constitutional rights and the Fifth amendment rights! https://www.washingtonpost.com/news/volokh-conspiracy/wp/2017/01/18/minnesota-court-on-the-fifth-amendment-and-compelling-fingerprints-to-unlock-a-phone/?noredirect=on&utm_term=.a5fe7809afed http://archive.is/QEsru Where is the changelog for such an important change? You cannot find anywhere that they got rid of ability to use passwords in exchange for fingerprint…. Then Moxie says it is impossible to do password app with “data encryption at rest” but that belies the years of documentation and literature including that of TextSecure (signal predessor) which clearly says inside the very app itself that the password is what encrypts and secures the text/data at rest!!!!! https://www.tomsguide.com/us/how-to-textsecure-encrypted-texts,news-18475.html http://archive.is/hzirQ Ever since the TExtSecure days, the OWN app itself says the passphrase IS used to encrypt the data at rest…. now the developer claims it was never the case? I say boycott Signal, I say Signal has been subverted to the dark side. I say Signal is CIA, I call BS .. Junkii7 commented on Aug 7, 2019 • edited Regarding your references, the credible Washington Post and The Intercept articles actually praise Signal. So your only reference is to tomsguide which is a joke compared to the other two. News flash, Signal is open source, so whatever security breach there is you can point it out in the code. As I’ve said on the forum “Did you know that the founder of the Chinese company Huawei was a member of the Peoples Liberation Army of China? China is one of the leaders in fake news.” Here are the articles- https://money.cnn.com/2016/05/20/technology/china-social-media-fake-posts-strategy/index.html https://www.theguardian.com/technology/2018/dec/08/the-giant-that-no-one-trusts-why-huaweis-history-haunts-it greyson-signal closed this on Aug 8, 2019 greyson-signal closed this on Aug 8, 2019 https://github.com/signalapp/Signal-Android/issues/8974 .. |
